haruspex
| Crates.io | haruspex |
| lib.rs | haruspex |
| version | 0.7.4 |
| created_at | 2024-11-22 11:43:29.728112+00 |
| updated_at | 2025-12-05 16:45:57.028196+00 |
| description | Vulnerability research assistant that extracts pseudocode from IDA Hex-Rays decompiler. |
| homepage | https://0xdeadbeef.info/ |
| repository | https://github.com/0xdea/haruspex |
| max_upload_size | |
| id | 1457309 |
| size | 51,868 |
documentation
https://0xdeadbeef.info/haruspex/haruspex/
README
haruspex
"Hacking is the discipline of questioning all your assumptions all of the time."
-- Dave Aitel
Haruspex is a blazing fast IDA Pro headless plugin that extracts pseudocode generated by IDA Pro's decompiler in a format that should be suitable to be imported into an IDE, or parsed by static analysis tools such as Semgrep, weggli, or oneiromancer.
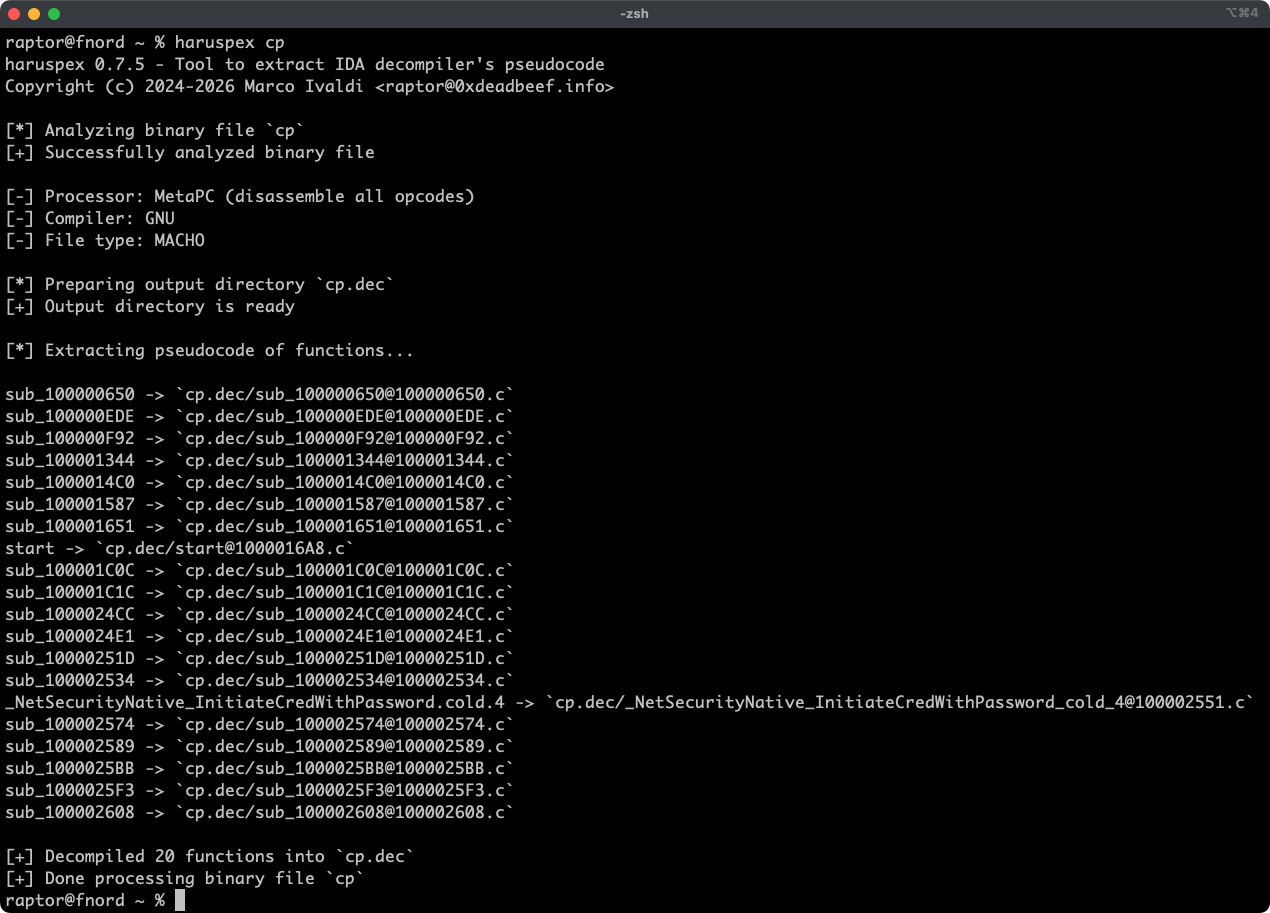
Features
- Blazing fast, headless user experience courtesy of IDA Pro 9.x and Binarly's idalib Rust bindings.
- Support for binary targets for any architecture implemented by IDA Pro's Hex-Rays decompiler.
- Pseudocode of each function is stored in a separated file in the output directory for easy inspection.
- External crates can invoke [
decompile_to_file] to decompile a function and save its pseudocode to disk.
Blog posts
- https://hex-rays.com/blog/streamlining-vulnerability-research-idalib-rust-bindings
- https://hnsecurity.it/blog/streamlining-vulnerability-research-with-ida-pro-and-rust
See also
- https://github.com/0xdea/ghidra-scripts/blob/main/Haruspex.java
- https://github.com/0xdea/semgrep-rules
- https://github.com/0xdea/weggli-patterns
- https://docs.hex-rays.com/release-notes/9_0#headless-processing-with-idalib
- https://github.com/binarly-io/idalib
- https://github.com/xorpse/parascope
- https://hnsecurity.it/blog/automating-binary-vulnerability-discovery-with-ghidra-and-semgrep
Installing
The easiest way to get the latest release is via crates.io:
- Download, install, and configure IDA Pro (see https://hex-rays.com/ida-pro).
- Install LLVM/Clang (see https://rust-lang.github.io/rust-bindgen/requirements.html).
- On Linux/macOS, install as follows:
On Windows, instead, use the following commands:export IDADIR=/path/to/ida # if not set, the build script will check common locations cargo install haruspex$env:LIBCLANG_PATH="\path\to\clang+llvm\bin" $env:PATH="\path\to\ida;$env:PATH" $env:IDADIR="\path\to\ida" # if not set, the build script will check common locations cargo install haruspex
Compiling
Alternatively, you can build from source:
- Download, install, and configure IDA Pro (see https://hex-rays.com/ida-pro).
- Install LLVM/Clang (see https://rust-lang.github.io/rust-bindgen/requirements.html).
- On Linux/macOS, compile as follows:
On Windows, instead, use the following commands:git clone --depth 1 https://github.com/0xdea/haruspex cd haruspex export IDADIR=/path/to/ida # if not set, the build script will check common locations cargo build --releasegit clone --depth 1 https://github.com/0xdea/haruspex cd haruspex $env:LIBCLANG_PATH="\path\to\clang+llvm\bin" $env:PATH="\path\to\ida;$env:PATH" $env:IDADIR="\path\to\ida" # if not set, the build script will check common locations cargo build --release
Usage
- Make sure IDA Pro is properly configured with a valid license.
- Run as follows:
haruspex <binary_file> - Find the extracted pseudocode of each decompiled function in the
binary_file.decdirectory:vim <binary_file>.dec code <binary_file>.dec
Compatibility
- IDA Pro 9.0.240925 - Latest compatible: v0.2.4.
- IDA Pro 9.0.241217 - Latest compatible: v0.3.5.
- IDA Pro 9.1.250226 - Latest compatible: v0.6.2.
- IDA Pro 9.2.250908 - Latest compatible: current version.
Note: check idalib documentation for additional information.
Changelog
TODO
- Use the
.cppextension instead of.cto output pseudocode (see this issue)? - Integrate with Semgrep scanning (see https://github.com/0xdea/semgrep-rules).
- Integrate with weggli scanning (see https://github.com/0xdea/weggli-patterns).
- Improve decompiler output in the style of HexRaysPyTools and abyss.
- Implement parallel analysis (see https://github.com/fugue-re/fugue-mptp).




