trippy-core
| Crates.io | trippy-core |
| lib.rs | trippy-core |
| version | 0.13.0 |
| created_at | 2024-08-09 16:44:49.883801+00 |
| updated_at | 2025-05-05 12:47:01.688376+00 |
| description | A network tracing library |
| homepage | https://github.com/fujiapple852/trippy |
| repository | https://github.com/fujiapple852/trippy |
| max_upload_size | |
| id | 1331147 |
| size | 959,121 |
documentation
README



Trippy combines the functionality of traceroute and ping and is designed to assist with the analysis of networking
issues.
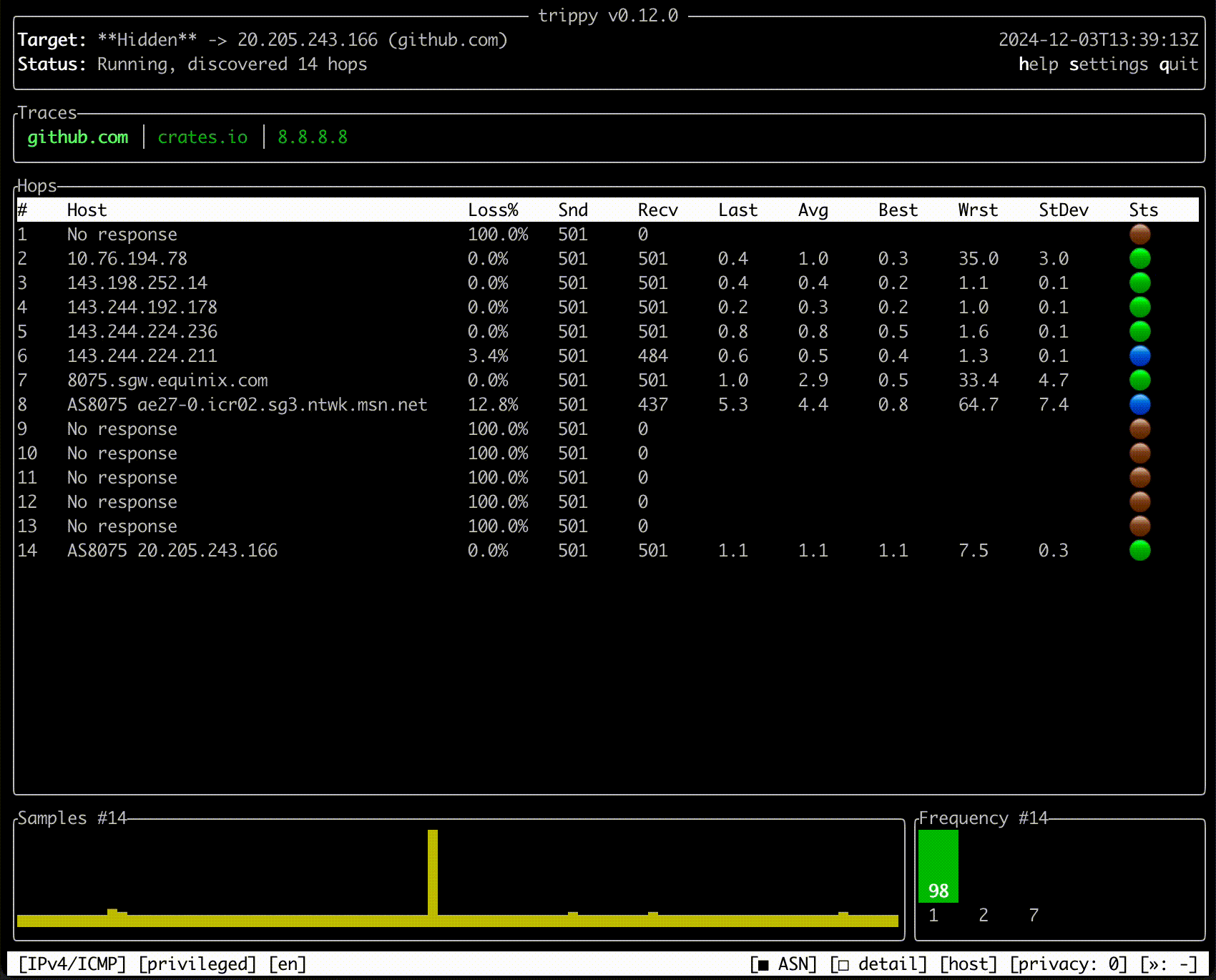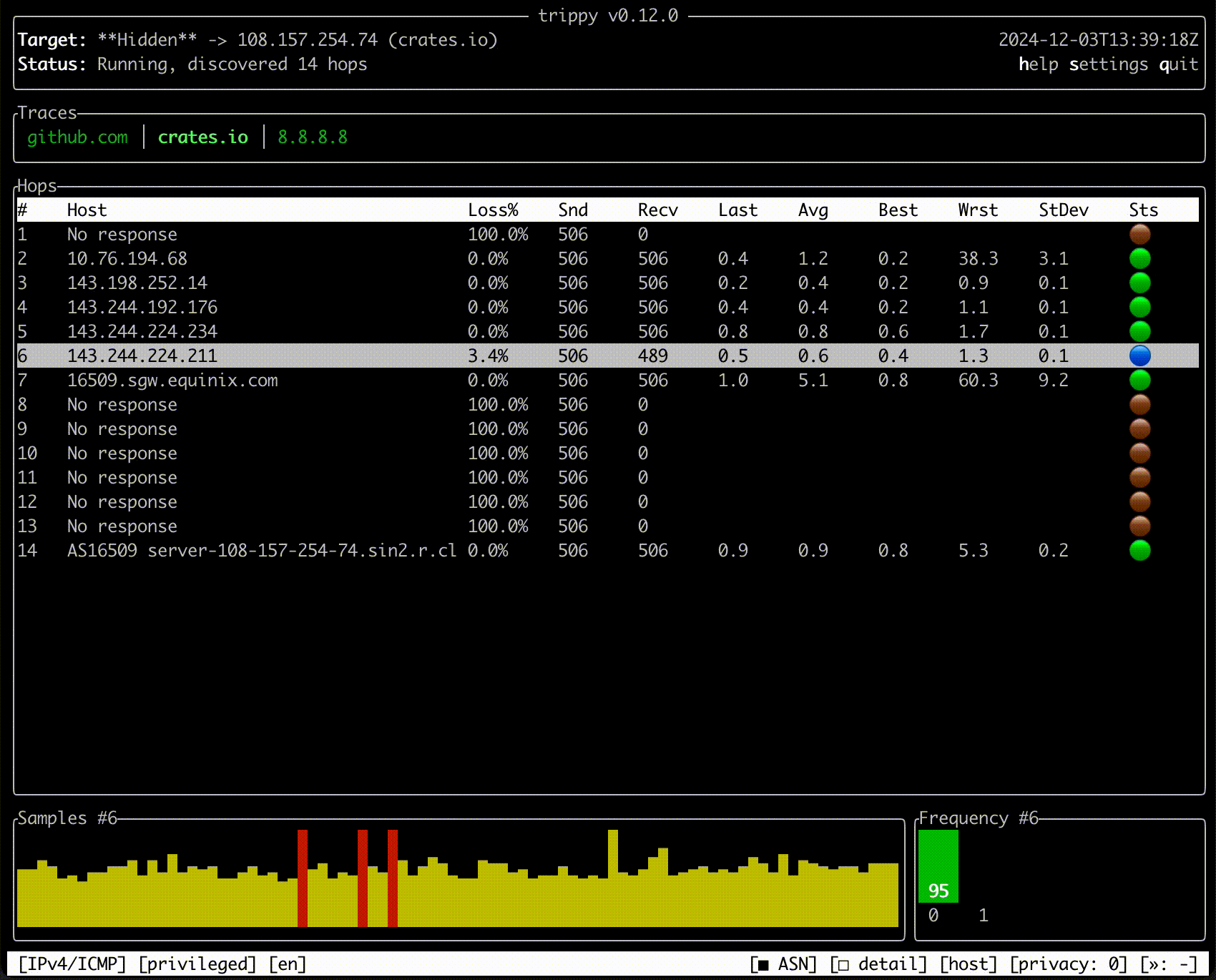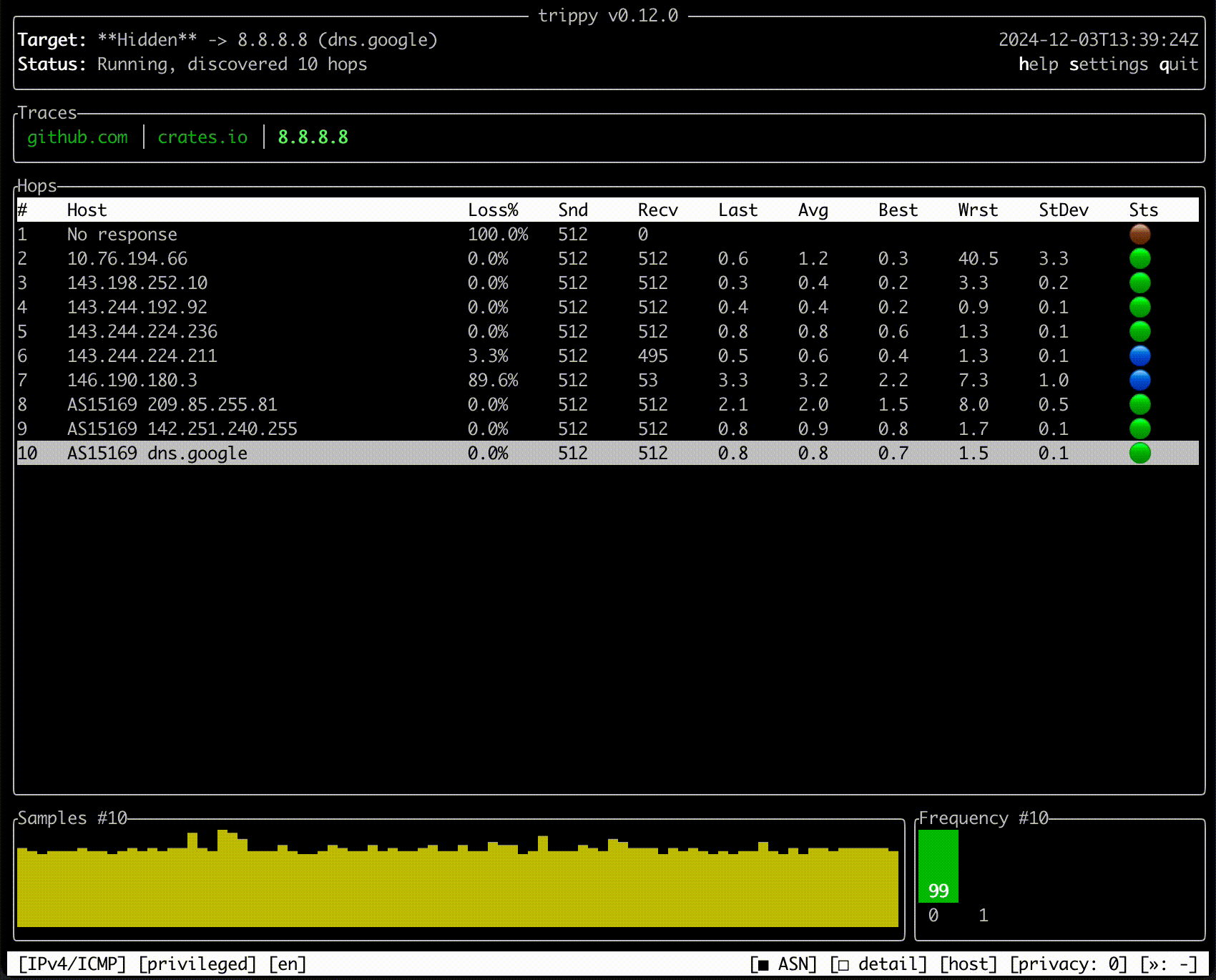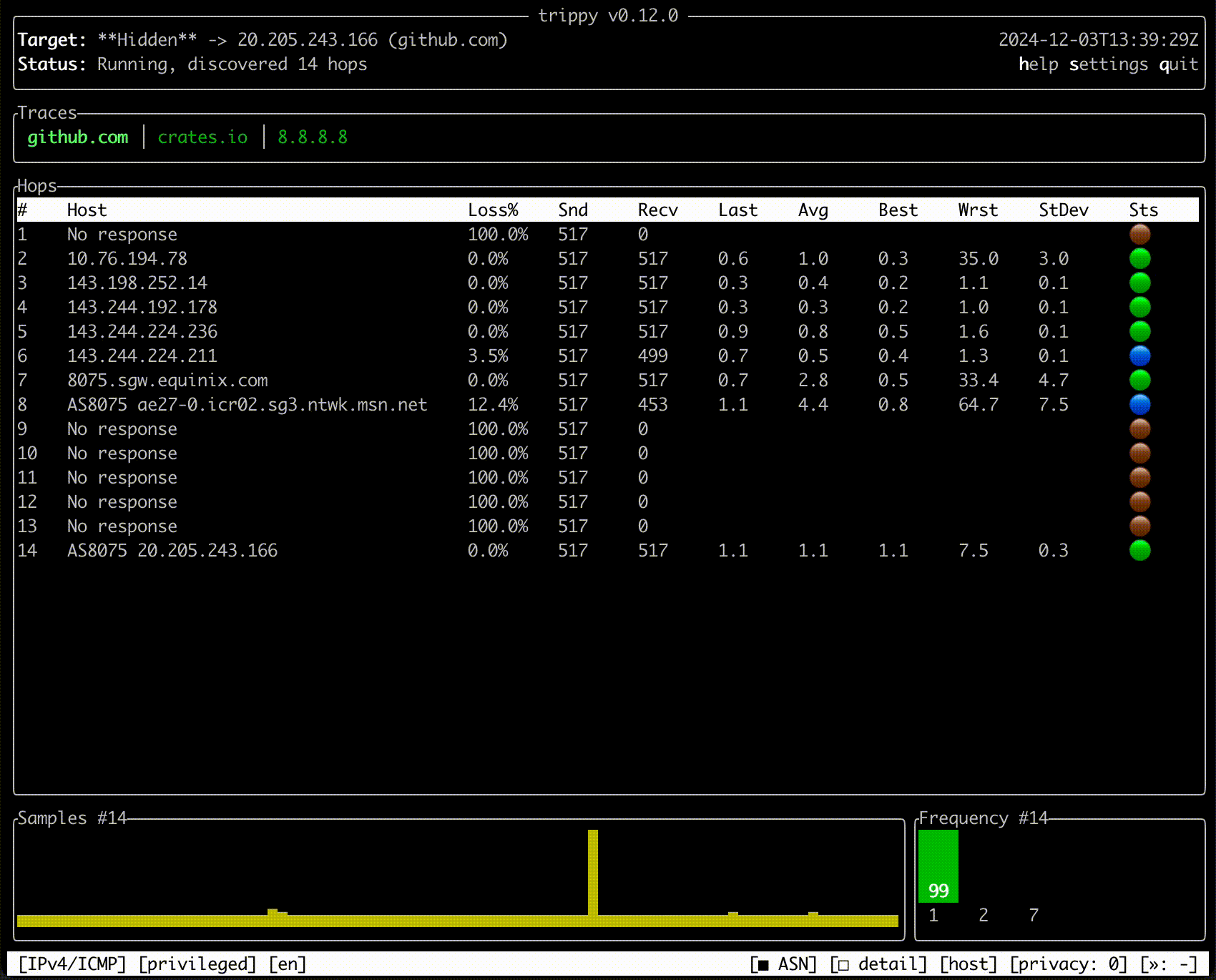
Quick Start
See the getting started guide.
Install
Trippy runs on Linux, BSD, macOS, and Windows. It can be installed from most package managers, precompiled binaries, or source.
For example, to install Trippy from cargo:
cargo install trippy --locked
All package managers
Cargo
cargo install trippy --locked
APT (Debian)
apt install trippy
ⓘ Note:
Only available for Debian 13 (
trixie) and later.
PPA (Ubuntu)
add-apt-repository ppa:fujiapple/trippy
apt update && apt install trippy
ⓘ Note:
Only available for Ubuntu 24.04 (
Noble) and 22.04 (Jammy).
Snap (Linux)
snap install trippy
Homebrew (macOS)
brew install trippy
WinGet (Windows)
winget install trippy
Scoop (Windows)
scoop install trippy
Chocolatey (Windows)
choco install trippy
NetBSD
pkgin install trippy
FreeBSD
pkg install trippy
OpenBSD
pkg_add trippy
Arch Linux
pacman -S trippy
Gentoo Linux
emerge -av net-analyzer/trippy
Void Linux
xbps-install -S trippy
ALT Sisyphus
apt-get install trippy
Chimera Linux
apk add trippy
Nix
nix-env -iA trippy
Docker
docker run -it fujiapple/trippy
All Repositories
See the installation guide for details of how to install Trippy on your system.
Run
To run a basic trace to example.com with default settings, use the following command:
sudo trip example.com
See the usage examples and CLI reference for details of how to use Trippy. To use Trippy without elevated privileges, see the privileges guide.
Documentation
Full documentation is available at trippy.rs.
documentation links
Getting Started
See the Getting Started guide.
Features
See the Features list.
Distributions
See the Distributions list.
Privileges
See the Privileges guide.
Usage Examples
See the Usage Examples.
Command Reference
See the Command Reference.
Theme Reference
See the Theme Reference.
Column Reference
See the Column Reference.
Configuration Reference
See the Configuration Reference.
Locale Reference
See the Locale Reference.
Versions
See the Version Reference.
Frequently Asked Questions
Why does Trippy show "Awaiting data..."?
See the Awaiting Data guide.
How do I allow incoming ICMP traffic in the Windows Defender firewall?
See the Windows Defender Firewall guide.
What are the recommended settings for Trippy?
See the Recommended Tracing Settings guide.
Acknowledgements
Trippy is made possible by ratatui ( formerly tui-rs), crossterm as well as several foundational Rust libraries.
Trippy draws heavily from mtr and also incorporates ideas from both libparistraceroute & Dublin Traceroute.
The Trippy networking code is inspired by pnet and some elements of that codebase are incorporated in Trippy.
The AS data is retrieved from the IP to ASN Mapping Service provided by Team Cymru.
The trippy.cli.rs CNAME hosting is provided by cli.rs.
The Trippy chat room is sponsored by Zulip.
Trippy logo designed by Harun Ocaksiz Design.
License
This project is distributed under the terms of the Apache License (Version 2.0).
Unless you explicitly state otherwise, any contribution intentionally submitted for inclusion in time by you, as defined in the Apache-2.0 license, shall be licensed as above, without any additional terms or conditions.
See LICENSE for details.
Copyright 2022 Trippy Contributors




